kong中提供了两种最基本认证方式,即用户密码认证, basic-auth及basic-auth-api,这两种方式非常好理解,使用的场景类似
basic-auth的认证方式是直接验证用户名密码
而basic-auth-api会将提交的用户名密码到指定的api接口认证,比如统一认证服务
basic auth可以为Route或者Service添加简单的用户名密码认证
要使用basic-auth,直接在ingress的annotations中添加plugins.konghq.com: xxx即可,在2.x的版本中, plugins.konghq.com已经被抛弃, 变成konghq.com/plugins
使用非常简单:
假设现在要有一个应用需要通过用户名才能访问, 则
创建kongConsumer及KongCredential
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| apiVersion: configuration.konghq.com/v1
kind: KongConsumer
metadata:
name: user1
namespace: demo-echo
annotations:
kubernetes.io/ingress.class: "nginx"
username: echo-user1
---
apiVersion: configuration.konghq.com/v1
kind: KongCredential
metadata:
name: user1-basic-auth
namespace: demo-echo
annotations:
kubernetes.io/ingress.class: "nginx"
consumerRef: user1
type: basic-auth
config:
username: user1
password: 123456
|
2.x的版本KongCredential正在被淘汰,建议使用credential Secrets
首先是申明了kongConsumer及KongCredential这两个对象,在kong中,
同时,需要申明kongplugin,
1
2
3
4
5
6
7
| apiVersion: configuration.konghq.com/v1
kind: KongPlugin
metadata:
name: user1-basic-auth
namespace: kong
disabled: false
plugin: basic-auth
|
之后则添加ingress
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| apiVersion: v1
items:
- apiVersion: extensions/v1beta1
kind: Ingress
metadata:
annotations:
kubernetes.io/ingress.class: nginx
plugins.konghq.com: user1-basic-auth
name: infra-model-manager-ingress
spec:
rules:
- http:
paths:
- backend:
serviceName: nginx-svc
servicePort: 30222
path: /
|
如果是basic-auth-api的话,则kongplugin为
1
2
3
4
5
6
7
8
9
10
11
| apiVersion: configuration.konghq.com/v1
config:
auth_url: http://infra-console.default:8087/v1/kong/authorization
keepalive: 60000
method: POST
retry_count: 3
timeout: 10000
kind: KongPlugin
metadata:
name: basicauth
plugin: basic-auth-api
|
效果为:
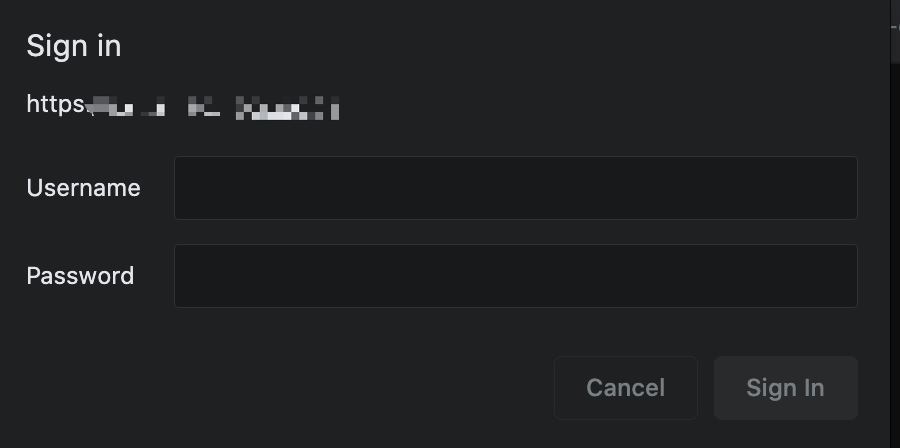
这个界面是不是很熟悉,没错,这个其实就是nginx的认证, kong本身就是基于nginxLUA的封装
如果密码输入错误的话,则会直接提示{"message":"Invalid authentication credentials"}
basic-auth-api的方式可以更好地把统一认证服务集成到应用中,这样避免每个服务都需要加入认证相关的代码.
参考文章:
